Nearly two weeks after it suffered a massive cyber attack, Optus has finally figured out who had which details leaked.
October 3, 2022

Nearly two weeks after it suffered a massive cyber attack, Optus has finally figured out who had which details leaked.
The Australian telco said in an update on Monday that of the 9.8 million current and former customers whose data was exposed, 2.1 million had at least one part of an identity document accessed, such as a driving licence or passport number. This is in addition to personal information including name, address, date of birth etc.
For approximately 1.2 million of those unfortunate people, it was a current and valid form of ID that was compromised. For the remaining 900,000, it was an expired ID. Optus said it has contacted these people and advised them on what action they need to take. Various press reports last week quoted Australian prime minister Anthony Albanese as saying that Optus has also agreed to cover the cost of replacing passports.
“The team at Optus is doing everything we possibly can to ensure that no harm comes to our customers as a result of this attack,” said Optus CEO Kelly Bayer Rosmarin, in a video hosted on her company’s Website.
Optus has also urged also the 7.7 million affected customers who were ‘lucky’ enough not to have their driving licence or passport leaked to remain vigilant.
“We are disappointed that even one customer’s information could be accessed, and we are deeply, deeply sorry that this could occur, especially because we genuinely care about safeguarding our customers’ information and we invest millions of dollars and have teams of people whose job it is to prevent something like this from happening,” Bayer Rosmarin said.
“That is why we have launched an independent review into what has occurred so we can understand what happened and make sure it doesn’t happen again and that we do better.”
Indeed, with the blessing of parent company Singtel, Optus has brought in Deloitte to conduct a forensic assessment of its security systems, which sounds a bit like digging through the smouldering ashes of a house in order to find the smoke alarm. The review aims to establish what went wrong and how the cyber attack was carried out.
“It will help inform the response to the incident for Optus. This may also help others in the private and public sector where sensitive data is held and risk of cyber attack exists,” said Bayer Rosmarin, in a separate statement. “I am committed to rebuilding trust with our customers and this important process will assist those efforts.”
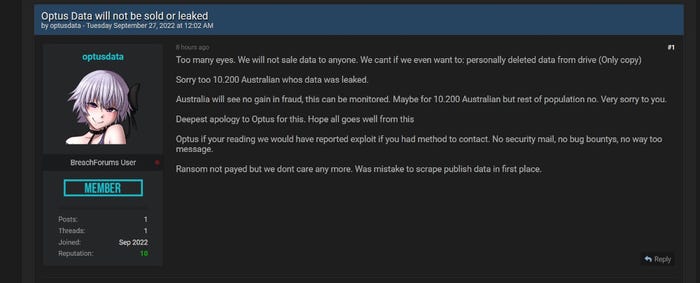
Meanwhile, the Optus hacker seems to have lost their bottle. In a post last week on the same data-breach forum they used to claim responsibility for the attack, the form member ‘optusdata’ said they no longer plan to sell the stolen data.
They claim to have deleted the only copy of the data cache, and issued an apology to affected customers and to Optus. It’s probably not a good idea to take a hacker at their word though, hence why Optus has told customers to remain on the lookout for suspicious activity. Nonetheless, it could prove to be a major let-off for the embattled Aussie telco.
Get the latest news straight to your inbox. Register for the Telecoms.com newsletter here.
About the Author(s)
You May Also Like








.png?width=300&auto=webp&quality=80&disable=upscale)


_1.jpg?width=300&auto=webp&quality=80&disable=upscale)


.png?width=800&auto=webp&quality=80&disable=upscale)