Kaspersky Labs unearths yet another state-linked malware
Cyber security specialists Kaspersky Labs has claimed to have discovered what it described as a highly-sophisticated cyberespionage campaign called Slingshot, which could have been active for six years.
March 12, 2018

Cyber security specialists Kaspersky Labs has claimed to have discovered what it described as a highly-sophisticated cyberespionage campaign called Slingshot, which could have been active for six years.
Clues in the text suggest the code was developed by English-speaking programmers, with the most likely source being a government intelligence agency. The team at Kaspersky believes activity started in at least 2012, and was active at the time of analysis in February six years later. The weak point of the perimeter has been traced back to Mikrotik routers and WinBox managing software, though it should be noted the cases thus far are the only ones which have been identified. Vulnerabilities could be in other bits of kit as well.
“The malicious samples investigated by the researchers were marked as ‘version 6.x’, which suggests the threat has existed for a considerable length of time,” the team said in a blog post.
“The development time, skill and cost involved in creating Slingshot’s complex toolset is likely to have been extremely high. Taken together, these clues suggest that the group behind Slingshot is likely to be highly organized and professional and probably state-sponsored.”
Perhaps one of the most interesting aspects of this malware is its ability to go undetected. Slingshot uses its own encrypted file system in an unused part of a hard drive, while it can also even shut down its components when it detects signs that might indicate forensic research. There are several little tricks the actors can use to avoid detection, which makes the malware particularly dangerous and tough to spot.
The attack itself starts with compromised routers made by MikroTik when downloading DLL files in the normal course of business. The actors figured out a way to add a malicious DLL to an otherwise legitimate package of other DLLs, which acted as a downloader for various malicious files which were stored in the router. MikroTik has been informed and fixed the issue, but Kaspersky believes this is not the only brand which was used during the campaign.
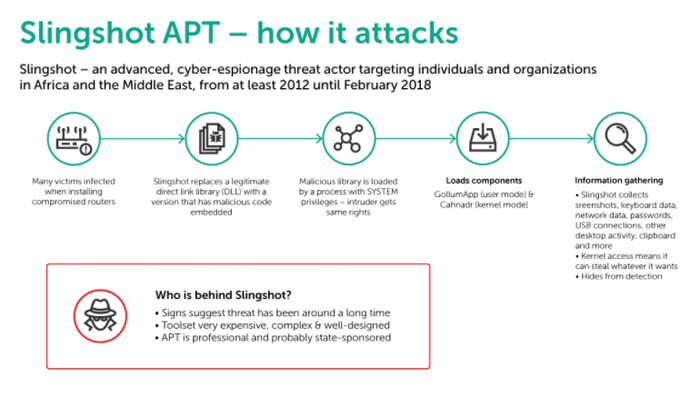
“Slingshot is very complex and the developers behind it have clearly spent a great deal of time and money on its creation,” said Kaspersky. “Its infection vector is remarkable – and, to the best of our knowledge, unique. We believe that most of the victims we observed appeared to have been initially infected through a Windows exploit or compromised Mikrotik routers.”
Two areas which Kaspersky believes to be particularly advanced are a kernel mode module called Cahnadr and GollumApp, a user mode module. Cahnadr runs in kernel mode giving attackers limitless control over the infected computer. It can also execute code without causing a blue screen (crashing the system) on the infected machine, which is highly unusual for malware. The second module, GollumApp, is even more sophisticated, containing nearly 1,500 user-code functions. Slingshot can collect screenshots, keyboard data, network data, passwords, other desktop activity, the clipboard, and a lot more.
The main purpose of this malware does seem to be counter-espionage, Kaspersky notes patterns consistent with other such examples, but because it operates in kernel there are no limitations to the information it can collect. Credit card numbers, password hashes and identification codes (such as social security numbers), are just a few examples, but it is essentially any dataset.
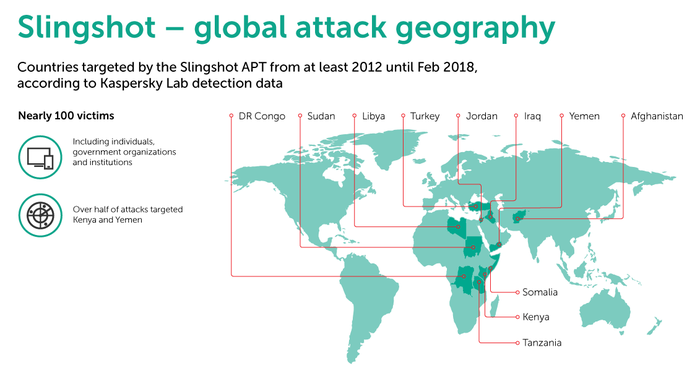
To date, Kaspersky has noted around 100 victims of Slingshot located in Kenya, Yemen, Afghanistan, Libya, Congo, Jordan, Turkey, Iraq, Sudan, Somalia and Tanzania. Interestingly enough, the vast majority of these instances are individuals not organizations or governments (though there are a few examples of the latter two).
Considering how advanced this malware is and it has been able to go undetected for six years, you have to wonder what else is hidden in the shadowy corners of the web. Hacking techniques and nefarious individuals have certainly advanced over this period, which is slightly concerning.
About the Author(s)
You May Also Like











_1.jpg?width=300&auto=webp&quality=80&disable=upscale)


.png?width=800&auto=webp&quality=80&disable=upscale)