It's looking more like the Internet of Threats at the moment – IBM
With 4G finally on the verge of being ubiquitous and 5G on the horizon the prospect of IoT is becoming real, but are organizations taking a genuinely thorough approach to security? New research from IBM does not suggest so.
March 13, 2018

With 4G finally on the verge of being ubiquitous and 5G on the horizon the prospect of IoT is becoming real, but are organizations taking a genuinely thorough approach to security? New research from IBM does not suggest so.
‘Building the plane while flying it’ is a phrase which we quite like from the report and while it is certainly an enviable strategy, there is risk of overlooking details. This is not to say companies should not be playing around with the ‘fail fast’ mentality, but attitudes towards security need to change drastically otherwise IoT will be nothing more than a liability.
This is not a new idea, but it is quite amazing that we are still complaining. For new technologies to be secure, for companies to be able to meet the privacy demands and for the industry to avoid another tsunami of data breaches, security needs to be built into the foundations of any proposition, product or service. Unfortunately security still seems to be considered little more than an afterthought; perhaps the emergence of IoT will make the previous years’ trend of data breaches seem like nothing more than a drop in the ocean?
IBM’s latest report is not incredibly detailed, but it doesn’t have to be. According to the research, 36% of executives rank IoT security as a top challenge for the business, so it is recognised. But we get the impression because it isn’t a revenue driving aspect of operations it is overlooked. The risk here is that IoT technologies are being deployed at a faster pace than they can be secured. When you look at the predictions you can see this is not just a stab-in-the-dark claim.
The IoT market is expected to grow from an installed base of 15 billion devices in 2015, through to 30 billion devices by 2020 and then onto 75 billion by 2025. While this massive rollout is gathering pace, there still isn’t really a comprehensive approach or solution to secure an organization from malicious intent.
Perhaps one of the most worrying statistics from the report is the ways in which companies are mitigating risk. The top strategy, with 45% of the respondents, is purchasing insurance. While this might satisfy the number men it is not addressing the security issue. Insurance will not stop a nefarious actor or protect your organization from an intrusion. This is the attitude to security which is worrying, many are just accepting it will happen, protecting themselves from the repercussions as opposed to actually doing anything to try and prevent it. It is quite a baffling approach.
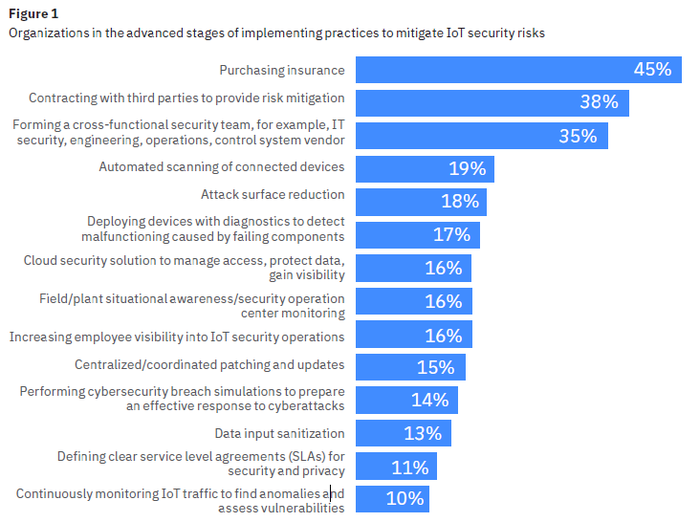
As you can see from the table above (taken from the report), it would be unfair to say that organizations are doing nothing, but IBM notes that there is so much more which can be achieved. Perhaps the biggest threat is an incomplete understanding of the risks posed by IoT deployments, which is natural in these early days. Maybe the best ways to move forward is to learn by doing as theoretical studies can only get you so far. Perhaps a more cautious approach would be advisable however.
There is of course a lot of work to be done, which is why we might see some disasters. To comprehensively secure your network against threats IBM notes every IoT endpoint must be identified and profiled, added to an asset inventory and monitored. It should be imperative to understand every gateway to the network, what it does and who it talks to; every connected device is a potential entry point and should be treated as a vulnerability. This will involve a lot of leg-work, a lot of time and money, so there will of course be cowboys who cut corners to steal a couple of yards on competitors. This is unavoidable, but hopefully the damage will be limited.
Most of the technology is already available. Threat detection software is available, machine learning algorithms can be written to monitor regular behaviour of devices/gateways and encryption techniques are common. There will need to be advances made but the foundations are there for a secure platform. Maybe we’re just about to find out who actually cares about security and who view it simply as a soundbite.
About the Author
You May Also Like










.png?width=300&auto=webp&quality=80&disable=upscale)


_1.jpg?width=300&auto=webp&quality=80&disable=upscale)