Nokia warns IoT malware infection rate has doubled
IoT adoption is taking off at a rapid pace, and so is the rate at which connected devices are being compromised by hackers.
October 22, 2020

IoT adoption is taking off at a rapid pace, and so is the rate at which connected devices are being compromised by hackers.
According to Nokia’s latest Threat Intelligence Report, IoT devices comprise 32.7 percent of infected devices on mobile networks, up from 16.2 percent in 2019. Windows PC’s claimed top spot with an infection rate of 38.9 percent; Android smartphones occupy third place with 26.6 percent.
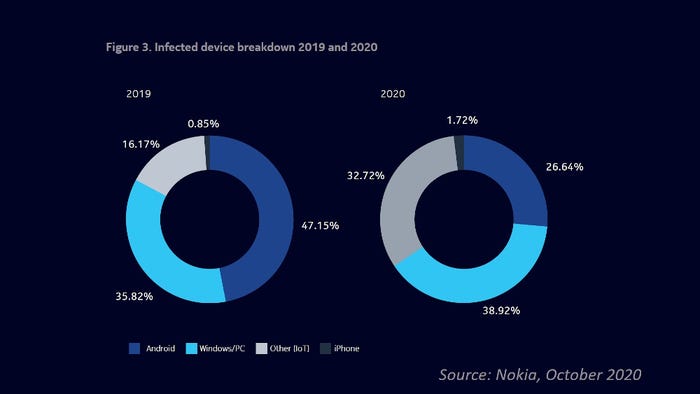
The Finnish vendor attributes the alarming rise to the usual culprits of poor cybersecurity practices on the one hand, and increasingly cunning attacks by hackers on the other.
Going into slightly more detail, Nokia said the vulnerability of an IoT device depends on whether it is visible to hackers that use network scanners.
“The rate of success in infecting IoT devices depends dramatically with the visibility of the devices to the Internet,” said Nokia, in its report. “In networks where devices are routinely assigned public-facing Internet IP addresses, we find a high IoT infection rate. In networks where carrier grade NAT (Network address translation) is used, the infection rate is considerably reduced, because the vulnerable devices are not visible to network scanning.”
With 5G expected to usher in massive machine-type communication (mMTC), the problem could get a lot worse, as the number of devices accessible directly from the Internet increases.
Furthermore, 5G networks by their very nature are potentially vulnerable, Nokia warned.
“The sweeping changes that are taking place in the 5G ecosystem open ample opportunities to malicious actors,” the company said. This is due to the fact that as cloud-native takes off, “the network infrastructure of communication service providers becomes more accessible to the attackers, so CSPs are increasingly targeted by sophisticated malicious actors.”
For instance, in a virtualised environment, compromised control applications “may wreak havoc on a large scale by erroneously or maliciously interacting with a central network controller,” Nokia said.
This has serious implications for 5G, given that we’re all supposed to be using it for everything in the not-too-distant future.
“The success of 5G depends on the capability to ensure not only a high level of security and privacy for subscribers, but also to combat various forms of attacks against the integrity and availability of the services these networks provide,” Nokia said.
In addition to IoT and 5G uptake, coronavirus has also provided hackers with an opportunity to hone their phishing skills.
According to Nokia’s report, February and March saw a 30 percent spike in the average monthly mobile infection rate, as hackers capitalised on peoples’ thirst for information about the spread of Covid-19. Examples include a trojan targeting Windows devices that masquerades as a map of coronavirus infections developed by John Hopkins University. Instead though it steals victims’ personal data. Nokia also found a similar one that installs ransomware on Android devices.
“Cybercriminals are playing on people’s fears and are seeing this situation as an opportunity to promote their agendas,” Nokia said.
Arguably it also suggests an absence of coordination, and indeed competence, from some central governments in their coronavirus response that has left people desperate for information from wherever they can get it – but that’s a rant for another day.
About the Author
You May Also Like





.png?width=300&auto=webp&quality=80&disable=upscale)




.png?width=300&auto=webp&quality=80&disable=upscale)


_1.jpg?width=300&auto=webp&quality=80&disable=upscale)