Matrix themed virus infects 25 million smartphones
A new variant of mobile malware, dubbed ‘Agent Smith’, which re-directs advertising funds to cybercriminals, has been identified and its infected 25 million smartphones already.
July 11, 2019

A new variant of mobile malware, dubbed ‘Agent Smith’, which re-directs advertising funds to cybercriminals, has been identified and its infected 25 million smartphones already.
Discovered by Check Point, this is a sneaky virus to deal with. Like ‘Agent Smith’ in the Matrix trilogy, the virus has the ability to consume a downloaded app and assume control.
Right now, the user is not being exploited in a direct manner. The presence of the virus does present dangers in terms of eavesdropping or credit fraud, but currently, the cybercriminals are using the virus to collect cash off advertisers through various trusted applications. The application is forced to display more adds than designed with the attackers collecting the additional credits.
“In this case, “Agent Smith” is being used to for financial gain through the use of malicious advertisements,” Check Point said on its blog.
“However, it could easily be used for far more intrusive and harmful purposes such as banking credential theft and eavesdropping. Indeed, due to its ability to hide its icon from the launcher and impersonate existing user-trusted popular apps, there are endless possibilities for this sort of malware to harm a user’s device.”
Check Point estimate that 25 million devices have been infected to date, the majority are in India and other Asia nations, although there have been identified devices in the US, UK and Australia. Although Check Point has not directly stated it, some have suggested the virus can be traced back to Guangzhou, China.
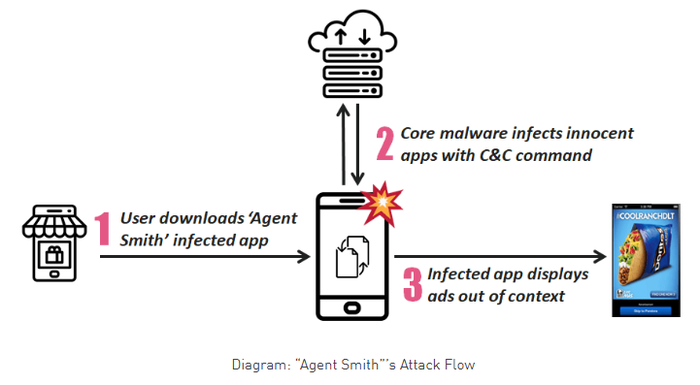 The virus itself works in three phases. Firstly, the user is encouraged to download a simplistic, free app (usually a minimal function game or sex-app) which contain an encrypted malicious payload. At this point, the malware searches the user’s device for any popular apps on a pre-determined list which can be targets at a later date.
The virus itself works in three phases. Firstly, the user is encouraged to download a simplistic, free app (usually a minimal function game or sex-app) which contain an encrypted malicious payload. At this point, the malware searches the user’s device for any popular apps on a pre-determined list which can be targets at a later date.
During the second phase, the malicious payload is decrypted into its original form and then abuses several known vulnerabilities without giving any clues to the user. Finally, the malware then attacks the pre-determined applications, extracting the innocent application’s APK file and then patches it with extra malicious modules.
‘Agent Smith’ was first detected in 2016 and the cybercriminals have seemingly been laying the groundwork for a larger attack for some time. It has certainly evolved over this period, and although Check Point has reported the malicious apps to the Google Security team, who is to say there are not more. The danger of ‘Agent Smith’ is that it is incredibly difficult to identify in the first place.
Perhaps this is an oversight in the security world which we will have to address before too long.
As it stands, numerous parties around the world are constantly on the look out for nefarious activity, however, in most cases the assumption is that it will be a state-sponsored attack. This does not seem to be the case here and perhaps why it is very difficult to detect the malware in the first place; everyone is looking for the wrong clues.
In this example, Check Point seem to have caught the suspect firm ahead of time, informing the Google Security team before any genuine damage has been done. That said, 25 million devices is still a substantial number but with the source identified it should be limited.
About the Author
You May Also Like


.png?width=300&auto=webp&quality=80&disable=upscale)







.png?width=300&auto=webp&quality=80&disable=upscale)


_1.jpg?width=300&auto=webp&quality=80&disable=upscale)