Accelerating Network slicing readiness between CSPs and HyperscalersAccelerating Network slicing readiness between CSPs and Hyperscalers

Sponsored Content
Intro
CSPs and hyperscalers are increasingly focused on expanding their service offerings and establishing new value chains. The landscape of emerging solutions will use a rich and diverse range of connectivity options and naturally converging strengths of the CSPs and hyperscalers. CSPs currently add to the value chain not only through their well-established physical infrastructure but also wireless connectivity and private cloud services, while the hyperscalers provide a plethora of public & edge cloud services (xNFs, AI/ML, database, data lakes, and edge) that enhance and accelerate the connectivity provided by the CSPs. Together the ensemble of both parties’ respective strengths will formalize a new generation of end-to-end solutions to expand their operations and business footprints and ability to jointly serve their extended addressable markets.
Mobile Private Networks and 5G have dominated future debates. CSPs have used, touted 5G to speed up their cloud-native transformation, monetize investments, and automate operations. The NEF or NESP with the right APIs will also help CSPs monetize their service capabilities. Thus, CSPs may use their traditional capabilities and current investments and optimize their engagement with hyperscalers.
The strategic capabilities are only further augmented by the advent of Network Slicing, which is the most anticipated cross-domain strategy that formalizes end-to-end service offerings that use both the CSP and hyperscaler resources by connecting domain-specific resources.
Let’s investigate how network slicing improves 5G monetization and accelerates market preparedness.
What is the market status of Network slicing?
1- A reminder of what is network slicing and its intended usage
Network slicing is a process for stitching resources across different telco service domains organized in network slice subnets, such as RAN, Transport, 5G Core, and even NFV, to create an end-to-end slice. Network segmentation is enabled by cross-domain OSS automation and orchestration, analytics generation (MDAF/NWDAF). In addition, it is facilitated by lower layer automation capabilities per domain: Service Management Orchestration (SMO) at Radio Access Network (RAN), Network Automation at Transport, and 5G/NFV orchestration referred to as Network Slice Subnets Management function (NSSMF). The cross-domain OSS infrastructure is the slicing manager or Network Slicing Management Function (NSMF) in the context of network slicing.
In short, Network slicing is a technique for leveraging operational and commercial capabilities from a BSS/OSS perspective that spans multiple domains. Properly supplied with hyperscaler orchestration capabilities, such as CloudFormation or Terraform, as part of their OSS service architecture, telcos are enabled to provide a cross-realm option that connects telcos and hyperscalers, thereby expanding telco operational and business footprints.
2- Current market activities for network slicing
Network slicing was commercialized worldwide in 2021 and 2022, contrary to popular belief, it is already a commercial reality. Early adopters have already built end-to-end network slicing management and a pricing and service model, affecting the African, American, Singaporean, Austrian, Swedish, and Japanese CSPs. These operators have introduced or are launching network-sliced FWA services, while others have created granular network-slicing service assurance.
OSS/BSS: What is its end-to-end role for network slicing?
It should be quite clear that network slicing or any other cross-domain solution such as Mobile Private Networks (MPN) is not possible without both a cloud-native alignment across domains and a cross-domain or multi-domain OSS service layer. Observability, xNF orchestration, an API framework, and tools have resulted from CNCF’s cloud-native principles’ worldwide consensus. This unanimity promises better automation and simpler operations. CSPs have started to abolish domain silos and are increasingly embracing cloud-native across domains to gain perspective and monetize the end-to-end service architecture. Despite the delayed disaggregation of the RAN domain, CSPs continue to reform themselves by adopting a more cautious approach, starting with vRAN and Cloud RAN before embracing Open RAN.
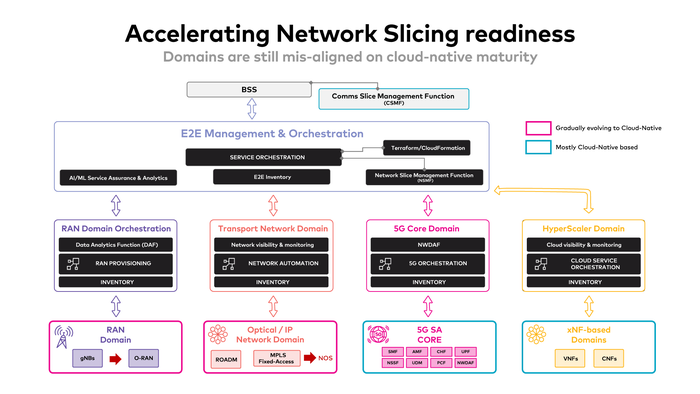
Fig.1: Cloud-native Misaligned domains
Next-generation CSP service architecture breaks technology and domain silos to let the OSS/BSS layers work their business and operational magic across domains. The 5G core domain “work” is already underway, and the move from 5G NSA to 5G SA will accomplish this cloud-native development or transition. However, RAN and Transport are tackling this at different paces and with distinct goals, as discussed in the following chapters. Cloud-native for RAN domains and Transport is aimed to simplify operations and organically minimize operational costs for orchestration, service fulfillment, observability, data for closed-loop automation, and service intelligence. CSPs would struggle to grow with hyperscalers without such improvements.
A uniform cloud-native set of principles across all CSP service domains enables BSS and OSS layers to provide a common business and operational umbrella to fulfill all domains’ needs for managing end-to-end solutions throughout the CSP realm. CSP solutions are then increasingly enabled to expand their natural realm limits on a uniform cloud-native matrix managed by a true cross-domain OSS/BSS service layer. CSPs would surely expand their total addressable market by working with hyperscalers on the edge and hybrid cloud services.
Are RAN & Transport domains really on the path of cloud-native bliss?
As previously described, Network Slicing is an end-to-end process/function that has its necessity in a consistent cloud-native adoption across domains. It also manifests itself through the cross-domain automation capabilities provided by and supported by a top-down BSS/OSS strategy.
The RAN (Radio Access Network) domain is still generating issues about its cloud-native capabilities, API openness, interface specification, and multi-vendor capability. Open RAN, led by the O-RAN alliance, checks all the requirements, but its delayed industry adoption due to multi-vendor integration, and operational challenges. RAN automation is also required to be tightly anchored to this top-down OSS/BSS approach.
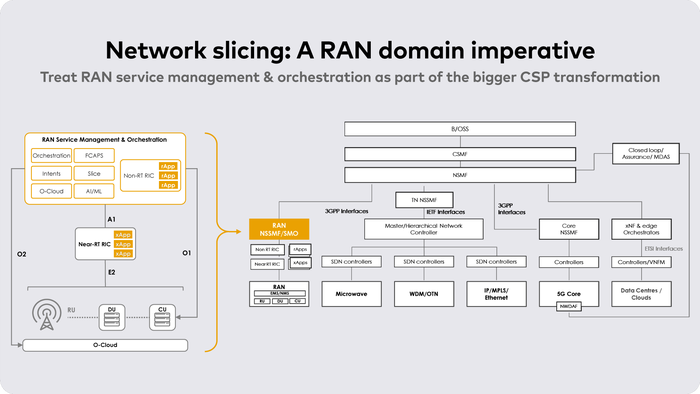
Fig.2: Open RAN SMO is an integral part of the OSS service layer
vRAN-based RAN domain disaggregation can be initiated by operators with a limited number (one or two) of vendors to manage the complexity of this transition. The primary objective, however, remains to make the RAN open and programmable. To automate, manage, and optimize RAN domain resources, the O-RAN alliance specifies Service Orchestration & Management (SMO) and RAN Intelligent Controller (RIC). SMO manages all disaggregated network functions of the RAN (Cloud, vDU, vCU), as well as RIC functions. The RIC is derived in two instances: the Non-RT RIC hosts rApps, functions as the operations’ center, and applies policies. The Nr-RT RIC hosts xApps and optimizes and reconfigures the assets of the disaggregated RAN.
On the transport domain, legacy vendors are slowly transitioning from Physical Network Functions (PNFs) to a cloud-native disaggregated and OSS-anchored transport domain. The typical applications for a disaggregated transport domain are Cell-Site routers, L3 MPLS services, and cloud networking solutions. However, IETF and other standards dictate the transport domain, which may not always align with wireless standards.
Hyperscalers: A key challenge and a tremendous opportunity
Hyperscalers are positioned at the intersection of CSPs and enterprises, with their ability to extend reach (cloud and edge) and to promote access to value-added functions (strict requirements, advanced storage, AI/ML, granular observability, and horizontal operations). As a result, cloud service providers are in a unique position to assist CSPs in expanding their operational and business footprints, as public or hybrid cloud services become an integral component of their network-slicing service capabilities.
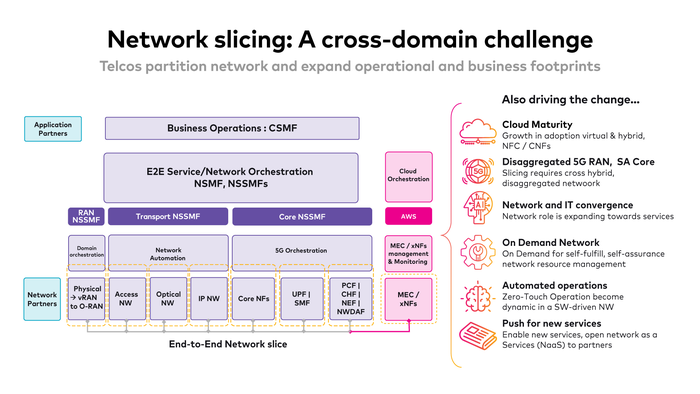
Fig.3: How a true end-to-end network slice looks like
Vendors and CSPs are engaged in a symbiotic relationship to progressively evolve from a hardware-centric service perspective to a software and cloud-native vision, as well as to break the domain boundaries by leveraging end-to-end automation capabilities. As described earlier in this document, these deliver cross-domain and extend value across realms (B2B: CSPs to hyperscalers) and B2B2X (CSPs to hyperscalers to enterprises).
Nevertheless, the role of hyperscalers extends beyond reach and value-add and could accelerate both network/service exposure as well as the development of new generations of solutions.
1 – How network slicing would benefit from network/service exposure?
As previously illustrated, Network Slicing primarily combines resource partitions from various service domains or realms. By crossing realms, CSPs expand their operational and business footprints with hyperscalers; this expansion of their traditional addressable market enables new opportunities. Hyperscalers offer enriched services and value-added solutions to CSPs, Carriers, and even enterprises, giving them a distinct position in the industry. Such an exotic location could provide hyperscalers with a terrific opportunity to facilitate exposure opportunities.
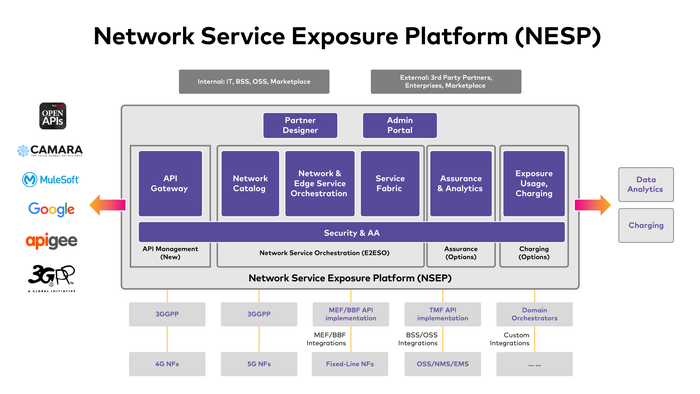
Fig.4: A Network Exposure Service Platform is part of a B/OSS ensemble
Exposure solutions extend CSP operational and commercial skills to capitalize on network slicing and new revenue prospects by developing new go-to-market approaches. Several exposure options exist:
• 5G Network Exposure Functions for 5G-specific exposure
This organically exposes network functions/applications via network APIs, creates an API composition catalog, and securely exposes service APIs to other parties like Hyperscaler marketplace ecosystems, CSP/carrier partners, or development platforms.
• Network-as-a-Service: While not new, Network-as-a-Service lets you design a collection of functions/apps that define a complete solution using APIs. A Network Exposure Service Platform (NESP) may expose these APIs as an abstraction layer from the OSS infrastructure layer. Hyperscalers provide trusted security to ensure market stickiness and replicability of the targeted solutions.
• Network-as-a-Platform, on the other hand, is a novel solution that meets the most demanding criteria for low latency, accurate device monitoring, optimal functions/app placement, strong privacy, and security, as well as cloud-native and disaggregation. The NaaP paradigm requires 3 key principles:
1) A single service model and catalog for business, network, and IT consistency
2)Abstracting network APIs like connection from service/product APIs
3) To benefit from a high-configurable model-driven orchestration paradigm that can accommodate B2C, B2B, and B2B2X delivery and management models
However, such a digital platform must comply with API standards that enable B2B and B2B2X collaboration, such as MEF, TMF, CAMARA, and TIP, and not be limited to proprietary APIs that would slow down or prevent CSPs and enterprises from reaching a multi-cloud and multi-vendor consensus. Thus, it would enable and accelerate new service innovations across domains/realms. As an example, facial recognition technologies might boost security at banks and other sensitive facilities. Also, due to the ubiquity of wireless connectivity, automotive manufacturers like BMW, Mercedes, Tesla, Acura, and others could be part of a cross-realm slice from CSPs to hyperscalers for commercial or governmental use.
2- Are hyperscalers a converging place for value-created solutions?
If we further broaden our perspective on the opportunities afforded by the hyperscalers’ privileged position, gradually, a pattern emerges in which all market participants (CSPs, Enterprises, Independent Software Vendors, Network Equipment Providers, and Hyperscalers) contribute their respective weights to mutually enrich services. The optimal location for most business engagements is often the median or the point where all parties agree to capture the essence of what they offer.
With that in mind, Hyperscalers are not only a location for service enhancement (AI/ML, Storage, xNF services, analytics, developer tools, IoT, security) but also a location where CSPs can extend their reach (edge, VPC, Content delivery, low-latency requirements) and increase the value of their physical wireless/wireline connectivity assets. They provide a place where enterprises (of any scale) can utilize newly developed solutions such as Mobile Private Networks, Network Slicing, Hybrid Cloud, edge solutions, etc.
Conclusion
Several operators regard hyperscalers as THE opportunity to leverage their existing assets and resources to innovate further and expand their respective value chains. It makes sense that they would target a solution such as network slicing to demonstrate their intention to expand their services and revenue beyond connectivity. However, it is frequently risky to rely solely on the location of value creation as the ultimate solution, rather than examining our capabilities.
Partnering with hyperscalers can positively contribute to the expansion of cloud, telco, and hybrid market opportunities, of which we currently see only the tails, to the benefit of all stakeholders. However, the most effective method for CSPs to secure their strategies is to implement the necessary changes described in earlier chapters, namely cloud-native, multi-domain business, and operational capabilities, disaggregated RAN, and the adoption of analytics and service assurance. I’m sure you’re thinking, Wait, you haven’t discussed service assurance yet, but this will have to wait for another paper or refer to this one.
Please visit our Amdocs Network website in the meantime and let us amaze you with everything we can do to facilitate your transition to a fully automated networking world.
About the Authors
You May Also Like










.png?width=300&auto=webp&quality=80&disable=upscale)


_1.jpg?width=300&auto=webp&quality=80&disable=upscale)