Security could be a fly in the ointment for the IoT boom
Cyber security firm CUJO AI has produced a report on the state of cybersecurity. Telecoms.com got an early look at the findings and they paint a grim picture of the threats to IoT devices and home networks.
January 23, 2023

Cyber security firm CUJO AI has produced a report on the state of cybersecurity. Telecoms.com got an early look at the findings and they paint a grim picture of the threats to IoT devices and home networks.
There are no shortage of cyber security reports, all of which provide a snapshot representative of the general situation based on the information the security firm or analyst has access to, but as sample sizes go this is a large one. Called ‘Cybersecurity Report 2022: Consumer Devices Under Threat’ – the report is based on anonymized threat data from 1.8 billion connected devices and 40 million home networks which it’s product in some way interacts with, and the firm claims it is the largest overview of real-world home network threat data. This year it has focussed on ‘device types and models that are outliers in the number of threats they face.’
There is a ton of data captured, but the main takeaway seems to be around the additional cybersecurity threats presented by the boom in IoT products – with households filling up with connected gizmos, it would appear hackers are being provided with extra vectors of attack to try and scam people or steal data.
The report purports to look at the problem ‘through the lens of device types and models to provide a new way of approaching the problem, as some device types clearly face more threats due to their value, accessibility or known vulnerabilities.’
It is based on data for the six months between May 1st and November 1st – during which time it says it stopped 2,102,990,310 threats, or over 8,113 every minute. Yes that’s a bit of self-serving comms to show off the virility of the security product – but it does lend some credence to the claims it makes.
“Cybercriminals are finding new ways to victimize home users,” says Leonardas Marozas, Head of CUJO AI Security Research Lab. “These attacks are evolving, and it is only natural that many people struggle to find the tools to protect their devices, data, homes and businesses from digital threats – protecting smart equipment can be extremely difficult for the average user.”
As part of its number crunching it sometimes uses a threat index to come up with conclusions about particular data sets – it says it uses this to: “represent the ratio of average threats per device in a category. A group of devices with a threat index above or below 1.00 experiences more or fewer than average threats, respectively. For example, a device model with a threat index of 400 experiences 10 times more threats on average than a device with a threat index of 40.”
It’s a beefy document, the entirety of which will be available later in the month. In the meantime, we’ve picked out and summarised some key findings.
Trends
The report identifies three distinct trends in the home cybersecurity landscape. The first is that the spread of adware is growing and there have been extremely large spikes in activity over the past year. “An analysis of the last 12 months of Web Reputation data shows that several adware distributors had a 300% larger footprint in the second half of the year,” says the report.
The second is that the number of end-of-life, unsupported or outdated devices lying around is increasing, which is creating more risk since IoT device lifetimes often exceed vendor support times, and protected or devices with unpatched vulnerabilities are very likely to be hacked.
And lastly it points to phishing as a major issue, claiming that every month, people in around 56% of homes attempt to open at least a single phishing link, which can lead to all sorts of financial and data breaches.
The report says while these are three different things (types of devices, vulnerabilities, and behaviours), they are connected since, for instance, ‘the growth of vulnerable IoT devices feeds into the prevalence of botnets and DDoS attacks.’
Brands
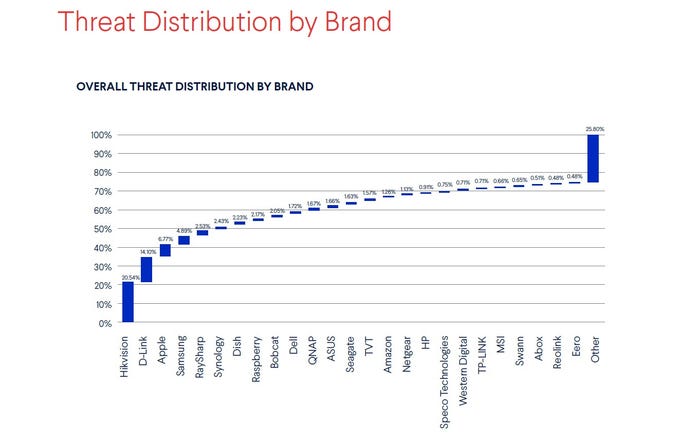
The report says that out of more than 4,359 device brands, 25 are being targeted by over 70% of all digital threats to consumer devices.
Hikvision topped that list (20.54%), followed by D-Link (14.1%), Apple (6.77%), and Samsung (4.89%). These are the four most attacked brands by the overall number of threats targeting them, though the report points out that there are a hell of a lot of Apple and Samsung devices out there – 89% and 73% of households having at least one, respectively.

Looking at the data through the threat index, Apple and Samsung devices experience ‘orders of magnitude’ fewer threats on average than Hikvision or D-Link devices. Seagate, Speco Technologies, QNAP, Hikvision, Bobcat, and TVT devices are among the most attacked brands by this metric, ‘with the first four drawing in over 300 times more threats on average than Dell devices.’
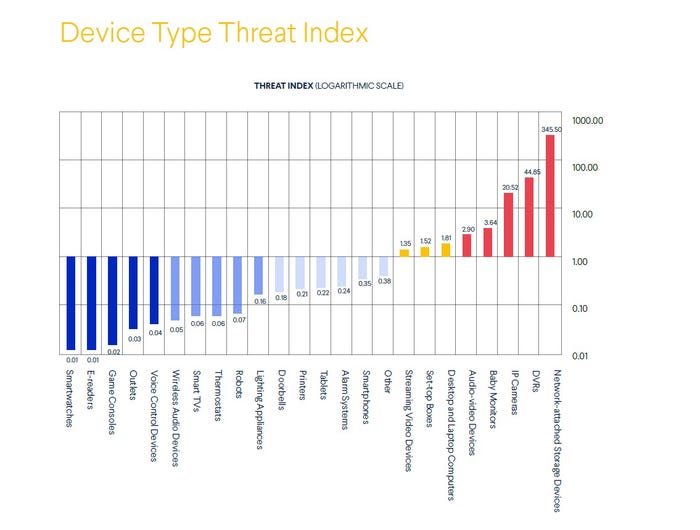
Device categories
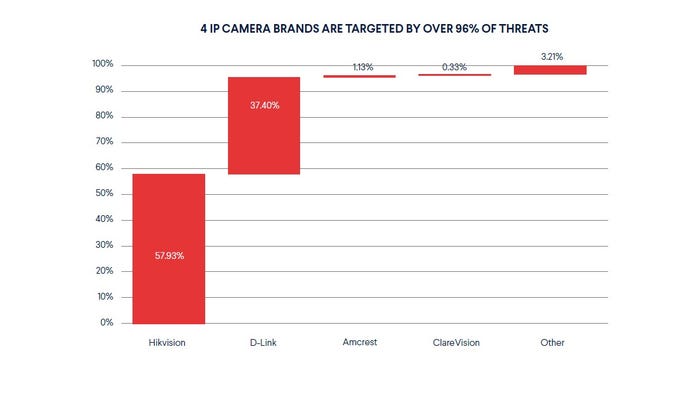
7 categories of device types are targeted by over 90% of all threats, we’re told. But while desktops, laptop computers, and smartphones make up close to 60% of all devices, they are targeted by a lower percentage of threats than that (45.85%). IP Cameras on the other hand, which make up just 1.2% of all devices, are targeted by a whopping 24% of malicious activities on consumer networks.
“IP cameras are famous for having poor security,” says the report. “They are being hacked not only to spy on people, but also to participate in coordinated DDoS attacks. Infected IP cameras also often become part of botnets. Many IP cameras have poor configurations, such as publicly known hard-coded administrator credentials, which make them easy targets for brute-force attacks.
Since, like NAS devices, IP cameras are accessed remotely by their users, they are often exposed to the Internet. Like DVRs, many IP cameras autoconfigure the home router via UPnP to open ports to the Internet.”
Going by the threat index, network-attached storage (NAS), DVR, IP cameras, baby monitors, and audio-video devices come out as the 5 most targeted device types in terms of average number of threats to each device type.
Baby monitors were the subject of a few high profile scare stories in terms of security when they first emerged years ago – but the report says this is not just scaremongering: “Large hacks of baby monitors are often portrayed in the media and resonate within society, since these devices are placed in very private settings. Our data shows that baby monitors are indeed attacked very often, albeit not as often as NAS devices or IP cameras.”
In terms of the most threatened brands in this specific space, the report says: The threat landscape of baby monitors looks rather surprising, as our data clearly shows that just a few D-Link devices are being targeted by almost all (98%) of all threats to baby monitors.
Popular devices, such as smartphones, smartwatches, tablets, or computers, face orders of magnitude fewer threats than NAS devices or DVRs on average, we’re told.
Web 3
Web 3 is one of the tech buzz words of the day, and while its not easy to define it very precisely, the report calls it ‘a new iteration of the World Wide Web based on decentralization and blockchain technologies.’ Crypto currencies and non-fungible tokens (NFTs) are the main things associated with it, and while they are extremely difficult to get your head around let alone explain, they have gathered fervent communities around them.
CUJO AI’s report has some water to pour on the scene however, claiming: “The transaction technologies used in Web3 applications are most often irreversible, making them a good environment for scammers – once a user is fooled into making a transaction, there is very little they can do to get their tokens back.
There is an entire shadow economy of Web3 scams, where scammers can buy or rent everything needed to run a scam… The CUJO AI Labs team expects Web3 scam numbers to grow significantly in the near future, as the number of Web3 scam websites discovered daily is slowly growing, according to our data.”
What does it all mean?
We can’t remember a time when cyberattacks were ever said to be going down, but it’s interesting to look at it all through the lens of the IoT sector specifically, which operates differently from laptops or smartphones.
These devices are relatively easy to keep up to date with the latest security software, as long as you do your updates when they pop up and keep your firewall on. This doesn’t make them invulnerable of course, but your Android or Apple phone is likely to have a patch ready quickly when vulnerabilities are discovered, and general updates are pretty regular.
The big consumer tech firms have been firing out IoT or smart home gizmos for years, however with recent attempts to unify them under one interoperability standard and the success of spearhead products like Amazon Echo, the whole sector has become pretty mainstream now.
The difference with these products is you can’t just install AVG on them, and certainly the average user is far less likely to even think about smart speakers or cameras in the contexts of security. And a big issue seems to be that with so many models across so many categories, security updates are not as simple as firing out a blanket iOS update which covers a lot of iPhones and iPads. Tech firms unleashed boat loads of IoT gadgets at CES, and at some point they will simply be unsupported and therefore much more vulnerable to a hack.
If it’s true the proliferation of them is providing easier ways for criminals to hack, phish, and scam, then that’s a problem. And if that problem becomes cemented in the minds of consumers, it could prove to be a fly in the ointment of a sector the tech industry has been trying to peddle for years.
Get the latest news straight to your inbox. Register for the Telecoms.com newsletter here.
About the Author(s)
You May Also Like











_1.jpg?width=300&auto=webp&quality=80&disable=upscale)


.png?width=800&auto=webp&quality=80&disable=upscale)